Approximately 5.6 million workers are at risk of exposure to bloodborne pathogens, such as Human Immunodeficiency Virus (the virus that causes AIDS), Hepatitis B Virus and Hepatitis C Virus. — Occupational Safety and Health Administration (OSHA) Read that again: 5.6 million workers are at risk. That’s a significant segment of the workforce. While public service... read more
The Smart Apps blog aims to educate and inform business owners on the benefits of using small business HR software for essential tasks. Whether it’s attendance, online hiring or employee recordkeeping, the HRdirect Smart Apps suite of tools has your small business covered.
Under the federal Occupational Safety and Health Act (OSHA), every employer is responsible for maintaining a safe, OSHA-compliant workplace. This involves following certain, industry-specific safety standards, in addition to providing safety training so employees have the skills and knowledge to safely do their work. The benefits of employee training cannot be overstated: Fewer workplace accidents,... read more
With numerous high-profile and alarming cases of harassment making news in recent years, the takeaways are clear. Workplace harassment is a pervasive issue across the nation, and businesses of all sizes must take proactive steps to prevent it. In addition to an anti-harassment policy, the most meaningful way to protect your business from problematic behavior... read more
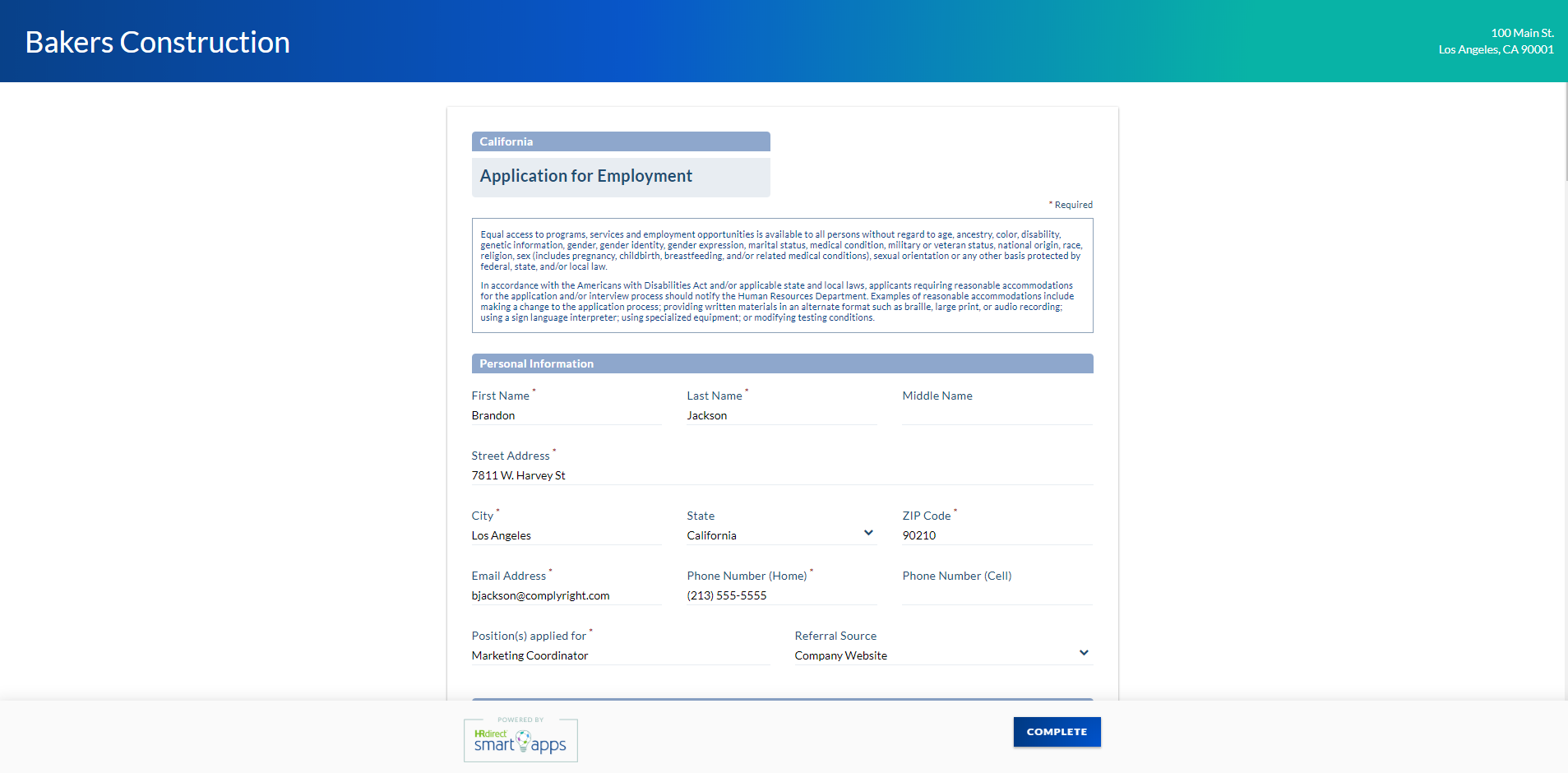
Everything is moving to the web these days – shopping, movie-watching, even job application management. Say what? It’s true. In our ever-evolving world of technology, you can now customize a job application that meets the specific needs of your business and manage the entire process from the comfort of your desktop. Even better: The right... read more
Placing ads … reviewing resumes … collecting applications … conducting interviews … checking references … It’s no wonder so many employers dread hiring! It’s a complicated undertaking with multiple stages to manage. That’s why more and more employers are relying on applicant tracking systems to turn that chaos into a consistent, cohesive process. What is... read more
Myth or fact? The world is flat. The sun revolves around the Earth. Ink on paper is the only legally acceptable signature. Strange as it seems, all three were once believed to be true. Today, all three are most definitely myths, and the last one may surprise you. Many small business owners believe ink signatures... read more